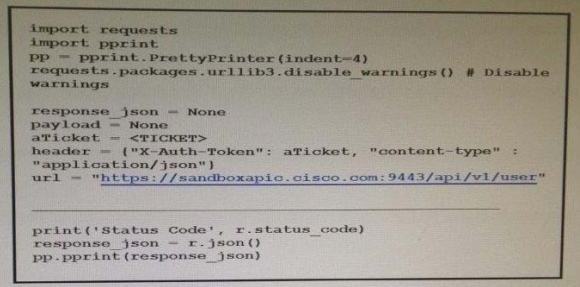
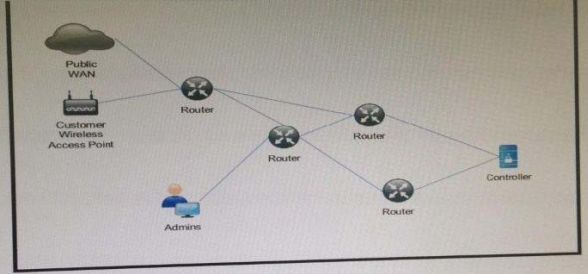
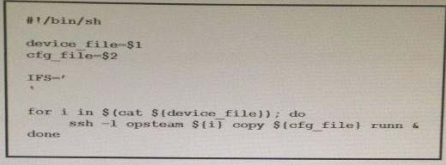
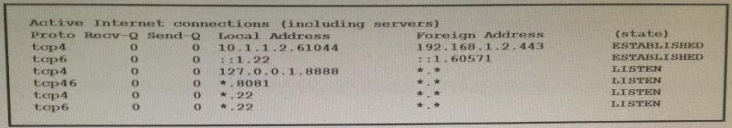
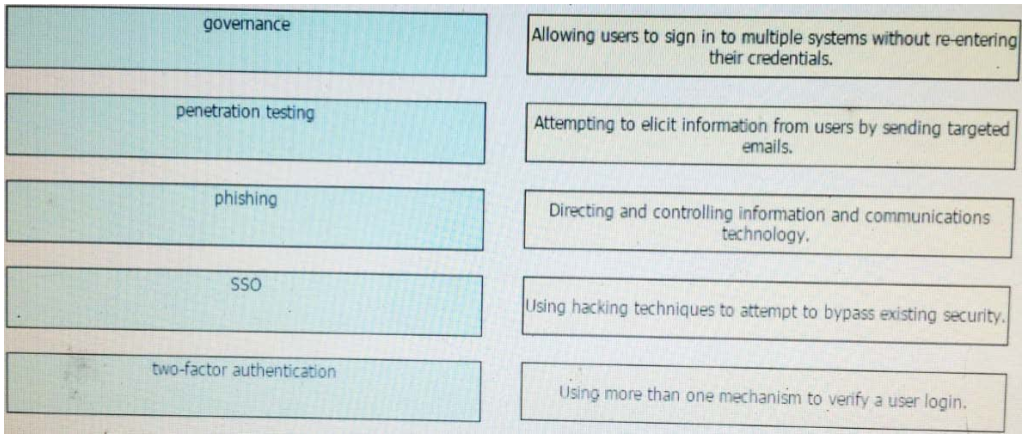
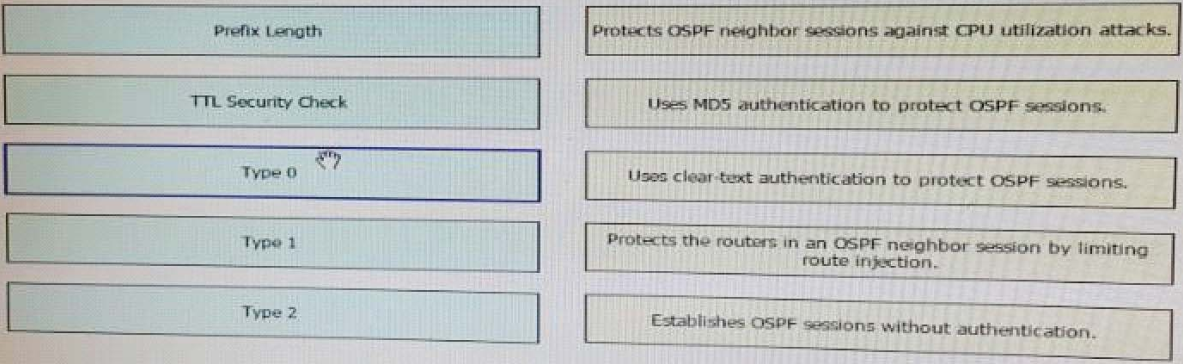
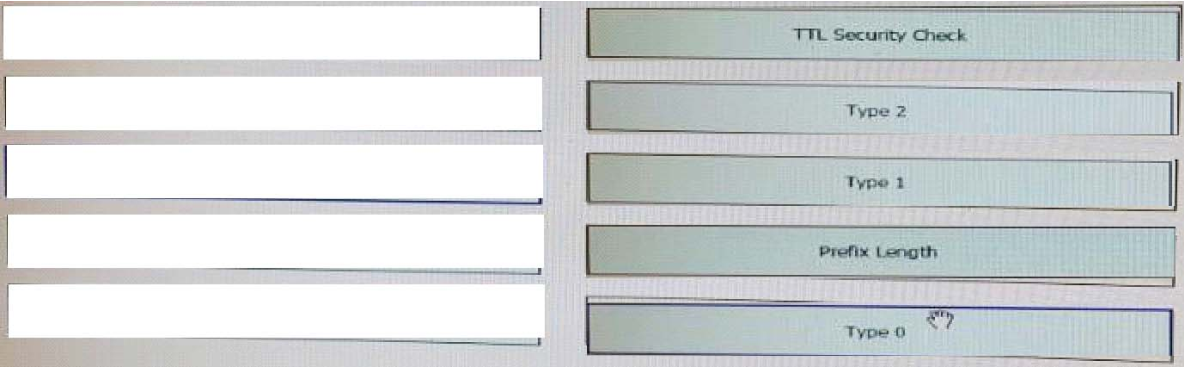
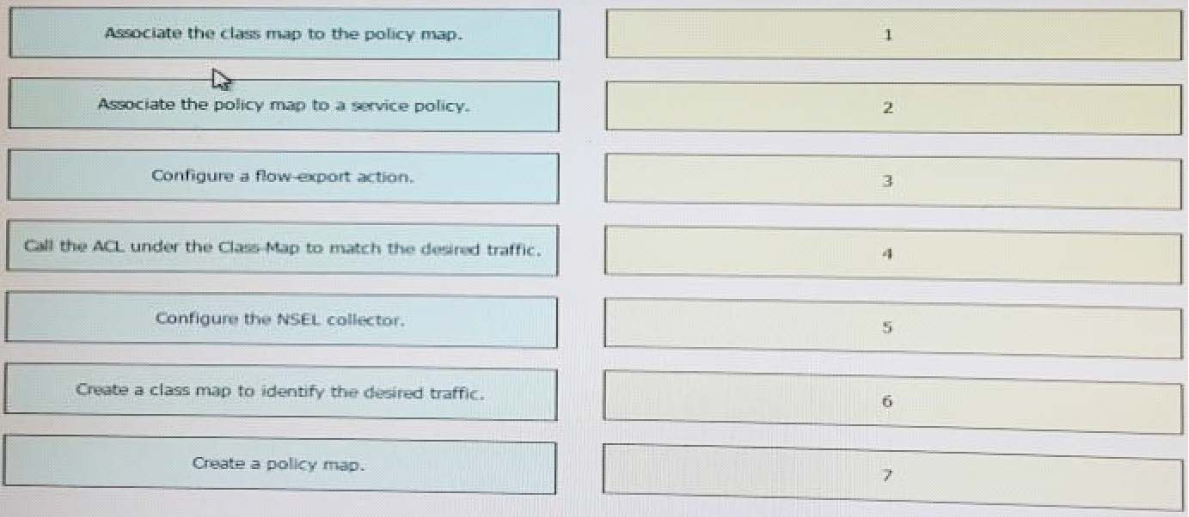
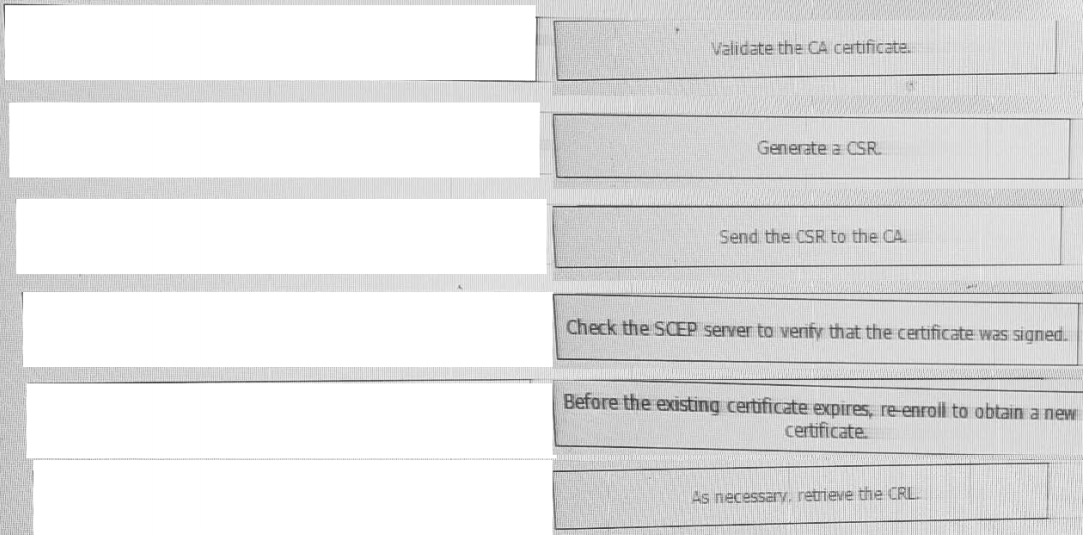
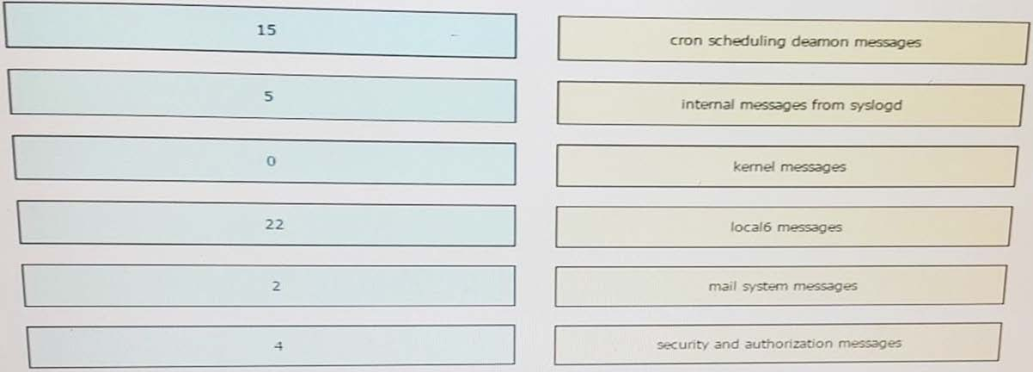
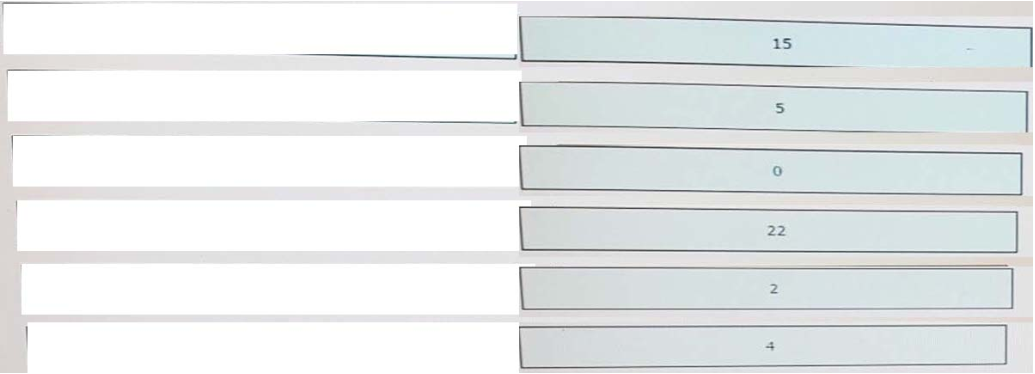
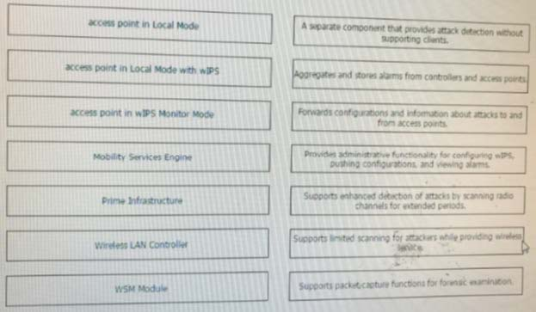
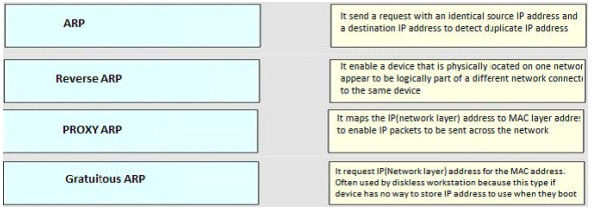
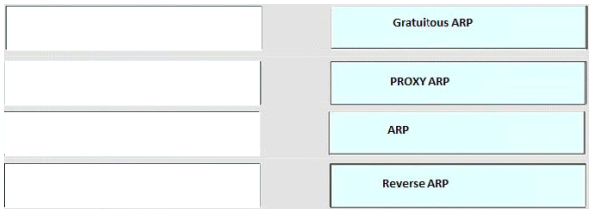
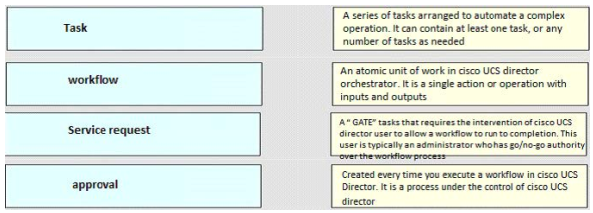
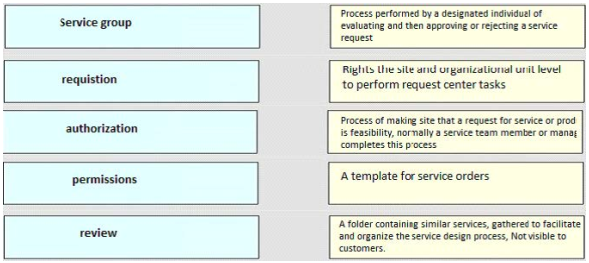
High quality latest Cisco CCNP Cloud 300-460 dumps exam real questions and answers free download from leads4pass. Practice for your Cisco CCNP Cloud 300-460 exam with the help of leads4pass, at leads4pass you can find all the necessary things for yourself that will help you to pass Cisco 300-460 exam.
“Implementing and Troubleshooting the Cisco Cloud Infrastructure” is the name of Cisco CCNP Cloud https://www.leads4pass.com/300-460.html exam dumps which covers all the knowledge points of the real Cisco exam. You can download Cisco CCNP Cloud 300-460 dumps pdf training material from leads4pass and pass the Cisco 300-460 exam in the first attempt. Cisco CCNP Cloud 300-460 dumps exam preparation kit contains all the necessary 300-460 questions that you need to know.
【Latest Cisco 300-460 dumps pdf materials from google drive】: https://drive.google.com/open?id=1Qrs3Vqtjs8Dwa7ZIuZV6Ob0HzdJPXFy8
【Latest Cisco 300-550 dumps pdf materials from google drive】: https://drive.google.com/open?id=1RFJnef4NKLu96YxCNZJI7HvYaqZryyYi
Vendor: Cisco
Certifications: CCNP Cloud
Exam Name: Implementing and Troubleshooting the Cisco Cloud Infrastructure
Exam Code: 300-460
Total Questions: 107 Q&As
New Cisco CCNP Cloud 300-460 Dumps Exam Real Questions And Answers (1-20)
QUESTION 1
A Cisco UCS Director administrator is changing the boot order in a boot policy. Which option lists the steps that accomplish this task?
A. On the menu bar, choose Physical > Storage.
In the left pane, expand the pod and then click the Cisco UCS Manager account.
In the right pane, click the Organizations tab.
Click the organization in which you want to modify a policy and then click View Details.
Click the Manage Boot Order tab.
Choose the boot policy that you want to clone and click Manage Boot Order.
B. On the menu bar, choose Physical > Compute.
In the left pane, expand the pod and then click the Cisco UCS Manager account.
In the right pane, click the Organizations tab.
Click the organization in which you want to modify a policy and then click View Details.
Click the Boot Policies tab.
Choose the boot policy that you want to clone and click Manage Boot Devices Order.
C. On the menu bar, choose Physical > Storage.
In the left pane, expand the pod and then click the Cisco UCS Manager account.
In the right pane, click the Organizations tab.
Click the organization in which you want to modify a policy and then click View Details.
Click the Boot Policies tab.
Choose the boot policy that you want to clone and click Manage Boot Devices Order.
D. On the menu bar, choose Physical > Compute.
In the left pane, expand the pod and then click the Cisco UCS Manager account.
In the right pane, click the Organizations tab.
Click the organization in which you want to modify a policy and then click View Details.
Click the Manage Boot Order tab.
Choose the boot policy that you want to clone and click Manage Boot Order.
Correct Answer: A
QUESTION 2
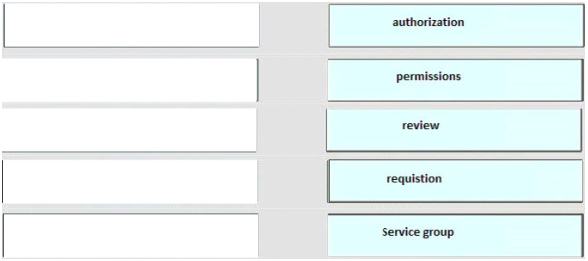
A Cisco UCS Director administrator is configuring vHBA. Which four fields are needed to configure vHBA? (Choose four.)
A. vHBA Name
B. Adapter Policy
C. Template Type
D. Organizations
E. Description
F. Fabric ID
G. UCS Organization Name
H. UCS Account Name
Correct Answer: ACEF
QUESTION 3
Which three options does the Cisco UCS Manager boot policy determine? (Choose three.)
A. initiator port range
B. selection of the boot device
C. location from which the server boots
D. initiator and target ports
E. global boot device priority
F. order in which boot devices are invoked
Correct Answer: BCF
QUESTION 4
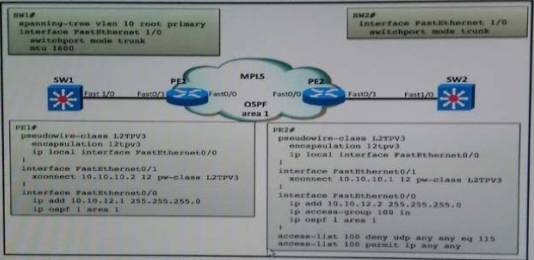
Refer to the exhibit.
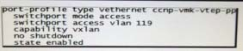
Which three commands complete the configuration for this Cisco Nexus 1000V port profile that is assigned to a vmkernel used for L3 VSM control plane? (Choose three.)
A. service-policy type qos output vmk-control
B. vmware port-group
C. system vlan 119
D. capability 13control
E. swithchport mode trunk
F. mtu 9000
G. swithchport 12control
Correct Answer: BCD
QUESTION 5
An administrator is installing a hypervisor and has provisioned a dedicated LAN connectivity, set the boot order, and is now rebooting the server to start installation. 300-460 dumps Which method is the administrator using to install the hypervisor?
A. host image mapping
B. KVM console
C. PXE installation
D. virtual boot
Correct Answer: C
QUESTION 6
An architect must choose a VXLAN architecture that utilizes hardware-based VXLAN adapters. Which type of architecture must be selected?
A. Layer 3
B. NSX
C. ACI
D. Layer 2
Correct Answer: C
QUESTION 7
Which three options describe the correct methods to install the Cisco Nexus 1000V VEM (VIB) software module on the VMware ESXi hypervisor? (Choose three.)
A. using the “Add Host to vSphere Distributed Switch” dialog on the vSphere Network tab when Update Manager is installed
B. esxcli software vib install –n/tmp/Cisco_bootbank_cisco-vem –v173-esx_5.2.1.3.1.4.0-3.2.1.vib
C. executing the Deploy-Nexus 1000V-VSEM.ps1 script
D. esxcli software vib install –v/tmp/Cisco_bootbank_cisco-vem –v173-esx_5.2.1.3.1.4.0-3.2.1.vib
E. using the Host Selection dialog box in Cisco Virtual Switch Update Manager
F. creating a baseline group in VMware Update Manager
Correct Answer: ADE
QUESTION 8
An engineer must ensure that all VXLAN and VTEP processes are kept on purpose-built hardware to ensure that all overlay functions are as fast as possible. In which solution is all VXLAN and VTEP decision making moved to the hardware, versus potentially slower software control?
A. Layer 3
B. ACI
C. NSX
D. Layer 2
Correct Answer: A
QUESTION 9
Which three statements about server pools are true? (Choose three.)
A. Cisco USC Director Displays only the managed servers in a server pool, but the size of the pool includes all servers.
B. Servers pools cannot be assigned to a Cisco USC Director group.
C. A given server can belong only to a specific server pool.
D. A server pool contains a set of servers that share the same attributes such as server type, amount of memory, local storage, type of CPU, or local drive configuration.
E. A server pool only includes servers from a specific chassis in the system.
F. If your system implements multitenansy through organizations, you can designate one ore more server pools to be used by a specific organization.
Correct Answer: ADF
QUESTION 10
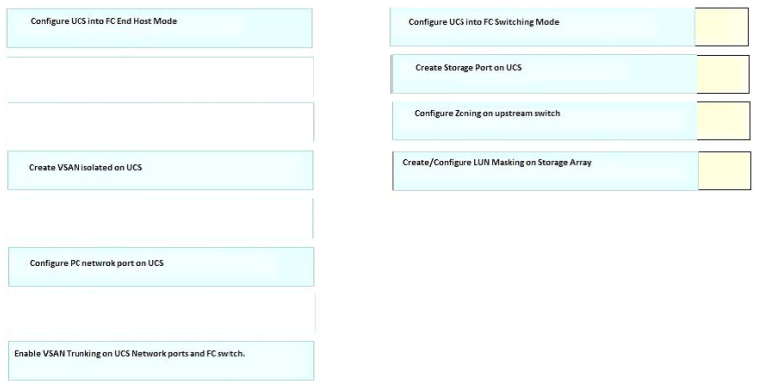
After implementing VXLAN VTEPs in a VMware NSX deployment, an engineer discovers that the VXLAN tunnel does not appear to function across the physical network. A pair of Cisco Nexus 5596UP Switches onnet the virtual network to the physical network. To permit the VXLAN tunnel to operate correctly, which action must the engineer take?
A. Upgrade Cisco Nexus to version 7.0 code.
B. Establish a dynamic routing protocol between the vSphere virtual router and the Cisco Nexus switches.
C. Remove storm control mechanisms that are blocking the establishment of the VXLAN tunnel.
D. Configure jumbo frame support on the Cisco Nexus switches.
E. Build a GRE tunnel to correctly encapsulate VXLAN between the networks.
Correct Answer: B
QUESTION 11
A Cisco UCS Director administrator is installing a Bare Metal Agent and is in the process of adding an NFS mount point. Which Administration menu option does the administrator choose to add an NFS mount point?
A. Compute Accounts
B. Storage Accounts
C. Physical Accounts
D. Bare Metal Accounts
Correct Answer: C
QUESTION 12
An engineer opens a KVM to a Cisco UCS B-Series Blade Server and boots off a Windows Server ISO with a virtual mapped drive. The server is not attempting to boot from the ISO.
What must the engineer modify first?
A. boot policy to KVM CD
B. BIOS policy to CD
C. boot policy to CD
D. local disk policy to CD
Correct Answer: A
QUESTION 13
Which four issues are often detected when validating workflows in Cisco UCS Director? (Choose four.)
A. Task Handler not found
B. missing administrator tasks or input tasks after import or upgrade
C. mapping mismatch
D. version incompatibilities
E. debugging logging information
F. missing optional values for tasks
G. missing task action value
H. missing mandatory values for tasks
Correct Answer: ABCH
QUESTION 14
A Cisco UCSM administrator has been tasked with deploying a new data center. Which two recommendations aid in the ability to associate a service with a server? 300-460 dumps (Choose two.)
A. The host control setting for a QoS policy applies to vNICs only. It has no effect on a vHBA.
B. You can assign only a QoS policy to a vHBA if the priority setting for that policy is set to fc, which represents the Fibre Channel system class.
C. The host control setting for a QoS policy applies to vHBAs only.
D. Power capping is supported for rack servers. If you include a power control policy in a service profile that is associated with a rack-mount server, the policy is implemented.
Correct Answer: BD
QUESTION 15
A Cisco UCS Director administrator is attempting to resolve a workflow validation issue. Which option lists the steps that accomplish this task?
A. On the menu bar, choose Policies > Catalogs.
Click the Activities tab.
Choose the workflow that failed validation.
Click Validate Workflow.
In the Workflow Validation dialog box, double click the description under Resolution.
In the Validation Errors dialog box, view the summary for the issue detected and complete the wizard to resolve the validation error.
B. On the menu bar, choose Policies > Orchestration.
Click the Activities tab.
Choose the workflow that failed validation.
Click Validate Workflow.
In the Workflow Validation dialog box, double click the description under Resolution.
In the Validation Errors dialog box, view the summary for the issue detected and complete the wizard to resolve the validation error.
C. On the menu bar, choose Policies > Orchestration.
Click the Workflows tab.
Choose the workflow that failed validation.
Click Validate Workflow.
In the Workflow Validation dialog box, double click the description under Resolution.
In the Validation Errors dialog box, view the summary for the issue detected and complete the wizard to resolve the validation error.
D. On the menu bar, choose Policies > Catalogs.
Click the Workflows tab.
Choose the workflow that failed validation.
Click Validate Workflow.
In the Workflow Validation dialog box, double click the description under Resolution.
In the Validation Errors dialog box, view the summary for the issue detected and complete the wizard to resolve the validation error.
Correct Answer: C
QUESTION 16
An engineer must create Cisco UCS service profiles for a new B-Series ESXi deployment. Which two configuration steps must be performed to isolate live migration traffic within a single Cisco UCS Fabric Interconnect? (Choose two.)
A. Install Cisco Nexus 1000V.
B. Enable fabric failover.
C. Create a single vNIC for the vSwitch.
D. Disable fabric failover.
E. Create one vNIC per fabric for the vSwitch.
F. Install VM-FEX.
Correct Answer: BF
QUESTION 17
Which Cisco Nexus 1000V configuration implements VxLAN segment 5001 as unicast and segment 5002 as multicast?
A. bridge-domain bd-5001
segment id 5001
no segment distribution mac
!
Bridge-domain bd-5002
segment id 5002
group 239.1.1.2
B. segment mode multicast
bridge-domain bd-5001
segment id 5001
segment mode unicast-only
!
Bridge-domain bd-5002
segment id 5002
group 239.1.1.2
segment mode multicast
C. segment mode unicast-only
bridge-domain bd-5001
segment id 5001
!
Bridge-domain bd-5002
segment id 5002
group 239.1.1.2
no segment mode unicast-only
D. segment mode unicast-only
bridge-domain bd-5001
segment id 5001
!
Bridge-domain bd-5002
segment id 5002
Correct Answer: C
QUESTION 18
A Cisco USCM administrator is creating a boot policy. Which option lists the steps needed to accomplish this task?
A. In the Navigation pane, click the Servers tab.
On the Servers tab, expand Servers > Policies.
Right-click Boot Policies and select Create Boot Policy.
B. In the Navigation pane, click the Equipment tab.
Expand Equipment > Rack-Mounts >Servers > Boot Policies.
Right-click Boot Orders and select Create Boot Policy.
C. In the Navigation pane, click the Servers tab.
On the Servers tab, expand Servers > Policies.
Click Boot Order and the Modify Boot Policy wizard displays.
Click Modify Boot Policy.
D. In the Navigation pane, click the Servers tab.
On the Servers tab, expand Servers > Policies.
Click Boot Security.
Click Modify Boot Policy.
Correct Answer: A
QUESTION 19
A Cisco UCS Director administrator is creating a VSAN. Which two types of VSANs are available? (Choose two.)
A. storage cloud
B. storage hybrid
C. SAN cloud
D. SAN
Correct Answer: CD
QUESTION 20
An engineer has designed a new Cisco UCS Director workflow to create a new Fibre Channel LUN and present it to ESXi hosts. After execution of the workflow, the LUN is not visible to the ESXi hosts. Which two actions must be taken to begin to troubleshoot the failed workflow? (Choose two.)
A. Look for information within vCenter Server under the Events tab for vCenter Server.
B. Look at the information that is produced in the rollback script that is associated with the failed workflow.
C. Look for information within vCenter Server under the Events tab for the applicable ESXi server.
D. Look for information within Cisco UCS Director under the Log tab of the Service Request Details window.
E. Look for information within Cisco UCS Director under the Input/Output tab of the Service Request Details window.
Correct Answer: AD
Useful latest Cisco CCNP Cloud 300-460 dumps exam practice files and study guides in PDF format free download from leads4pass. The best and most updated latest Cisco CCNP Cloud https://www.leads4pass.com/300-460.html dumps pdf training resources which are the best for clearing 300-460 exam test, and to get certified by Cisco CCNP Cloud. Download Cisco CCNP Cloud 300-460 dumps exam questions and verified answers. 100% passing guarantee and full refund in case of failure.
What Our Customers Are Saying:
You can click here to have a review about us: https://www.resellerratings.com/store/leads4pass
Why Select leads4pass?
leads4pass is the best site for providing online preparation material for 300-460 exam. Get your Cisco CCNP Cloud 300-460 exam prep questions in form of 300-460 PDF. Other brands started earlier, but the questions are outdated and the price is relatively expensive. leads4pass provide the latest real and cheapest practice questions and answers, help you pass the exam easily at first try.