High quality Cisco CCNA Cyber Ops 210-255 dumps exam questions and answers free download from leads4pass. Useful Cisco CCNA Cyber Ops 210-255 dumps pdf materials and vce youtube demo update free shared. “Implementing Cisco Cybersecurity Operations” is the name of Cisco CCNA Cyber Ops 210-255 dumps exam which covers all the knowledge points of the real Cisco exam. Cisco CCNA Cyber Ops 210-255 dumps exam preparation kit contains all the necessary 210-255 SECOPS Cisco questions that you need to know. Helpful newest Cisco CCNA Cyber Ops 210-255 dumps pdf training resources and study guides download free try, pass Cisco 210-255 exam test easily at the first time.
【Best Cisco 210-255 dumps pdf materials from google drive】: https://drive.google.com/open?id=0B_7qiYkH83VRTTJsYkV3c2xZb2s
【Best Cisco 210-250 dumps pdf materials from google drive】: https://drive.google.com/open?id=0B_7qiYkH83VRaF8zb0JFVmRVclU
Practice for your Cisco 210-255 exam with the help of leads4pass. You can download Cisco CCNA Cyber Ops 210-255 dumps pdf training material from leads4pass and pass the Cisco 210-255 exam in the first attempt. At leads4pass you can find all the necessary things for yourself that will help you to pass Cisco 210-255 exam. Cisco CCNA Cyber Ops 210-255 dumps exam preparation kit contains all the necessary 300-115 questions that you need to know.
Vendor: Cisco
Certifications: CCNA Cyber Ops
Exam Name: Implementing Cisco Cybersecurity Operations
Exam Code: 210-255
Total Questions: 80 Q&As
Cisco CCNA Cyber Ops 210-255 Dumps Exam Real Questions And Answers (Q1-Q30)
QUESTION 1
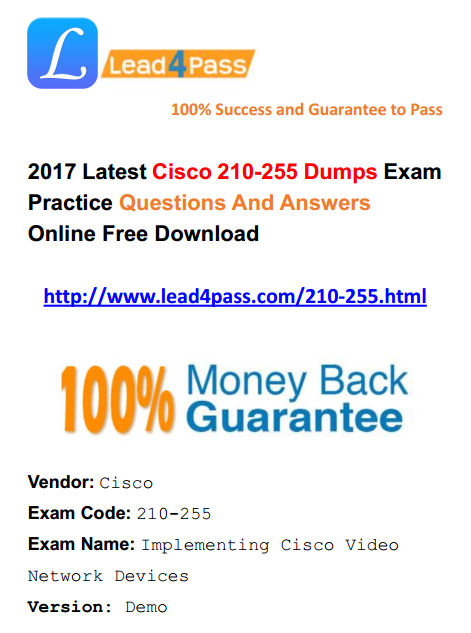
Refer to the exhibit. Which type of log is this an example of?
A. syslog
B. NetFlow log
C. proxy log
D. IDS log
Correct Answer: B
QUESTION 2
Which option creates a display filter on Wireshark on a host IP address or name?
A. ip.address == <address> or ip.network == <network>
B. [tcp|udp] ip.[src|dst] port <port>
C. ip.addr == <addr> or ip.name == <name>
D. ip.addr == <addr> or ip.host == <host>
Correct Answer: D
QUESTION 3
Which data element must be protected with regards to PCI?
A. past health condition
B. geographic location
C. full name
D. recent payment amount
Correct Answer: D
QUESTION 4
Which kind of evidence can be considered most reliable to arrive at an analytical assertion?
A. direct
B. corroborative
C. indirect
D. circumstantial
E. textual
Correct Answer: A
QUESTION 5
Which of the following is an example of a managed security offering where incident response experts monitor and respond to security alerts in a security operations center (SOC)?
A. Cisco CloudLock
B. Cisco’s Active Threat Analytics (ATA)
C. Cisco Managed Firepower Service
D. Cisco Jasper
Correct Answer: B
QUESTION 6
Which two options can be used by a threat actor to determine the role of a server? (Choose two.)
A. PCAP
B. tracert
C. running processes
D. hard drive configuration
E. applications
Correct Answer: CE
QUESTION 7
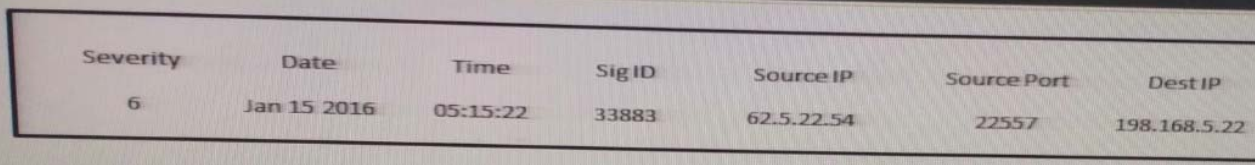
Refer to the Exhibit. 210-255 dumps A customer reports that they cannot access your organization’s website. Which option is a possible reason that the customer cannot access the website?
A. The server at 10.33.1.5 is using up too much bandwidth causing a denial- of-service.
B. The server at 10.67.10.5 has a virus.
C. A vulnerability scanner has shown that 10.67.10.5 has been compromised.
D. Web traffic sent from 10.67.10.5 has been identified as malicious by Internet sensors.
Correct Answer: C
QUESTION 8
Which option is a misuse variety per VERIS enumerations?
A. snooping
B. hacking
C. theft
D. assault
Correct Answer: A
QUESTION 9
Which Security Operations Center’s goal is to provide incident handling to a country?
A. Coordination Center
B. Internal CSIRT
C. National CSIRT
D. Analysis Center
Correct Answer: C
QUESTION 10
Which CVSSv3 metric captures the level of access that is required for a successful attack?
A. attack vector
B. attack complexity
C. privileges required
D. user interaction
Correct Answer: C
QUESTION 11
Which process is being utilized when IPS events are removed to improve data integrity?
A. data normalization
B. data availability
C. data protection
D. data signature
Correct Answer: B
QUESTION 12
Which source provides reports of vulnerabilities in software and hardware to a Security Operations Center?
A. Analysis Center
B. National CSIRT
C. Internal CSIRT
D. Physical Security
Correct Answer: C
QUESTION 13
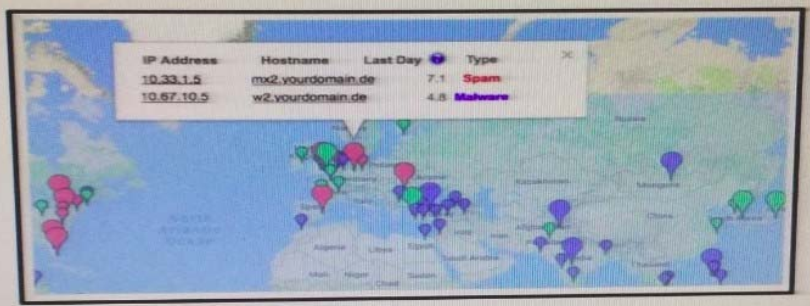
Drag and drop the type of evidence from the left onto the correct descnption(s) of that evidence on the right.
Select and Place:
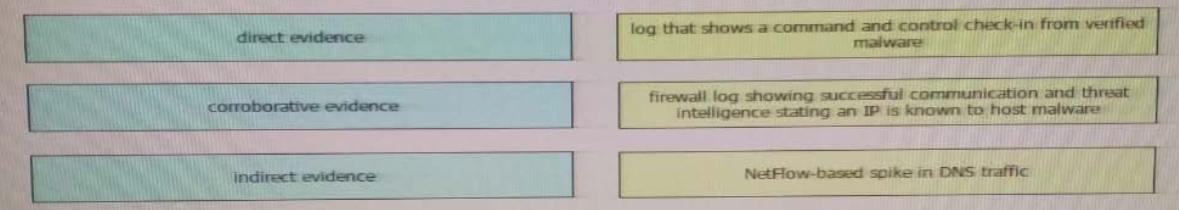
Correct Answer:

QUESTION 14
Refer to the exhibit. Drag and drop the element name from the left onto the correct piece of the NetFlow v5 record from a security event on the right.

Select and Place:

Correct Answer:

QUESTION 15
From a security perspective, why is it important to employ a clock synchronization protocol on a network?
A. so that everyone knows the local time
B. to ensure employees adhere to work schedule
C. to construct an accurate timeline of events when responding to an incident
D. to guarantee that updates are pushed out according to schedule
Correct Answer: A
QUESTION 16
210-255 dumps Which string matches the regular expression r(ege)+x?
A. rx
B. regeegex
C. r(ege)x
D. rege+x
Correct Answer: A
QUESTION 17
Which two HTTP header fields relate to intrusion analysis? (Choose two).
A. user-agent
B. host
C. connection
D. language
E. handshake type
Correct Answer: BC
QUESTION 18
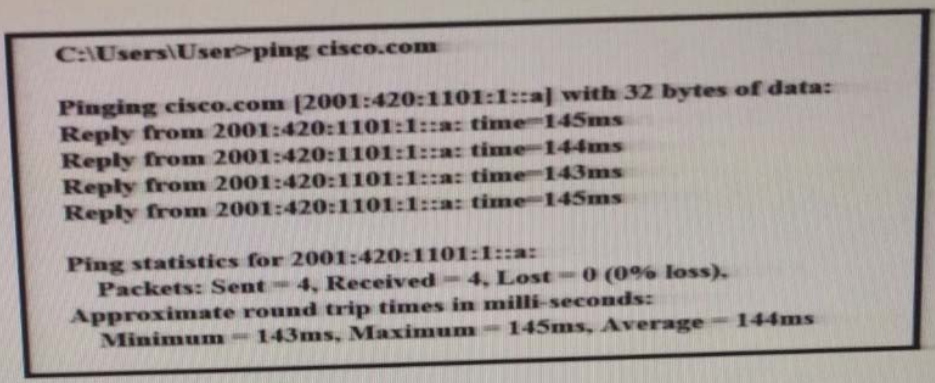
Refer to the exhibit. What can be determined from this ping result?
A. The public IP address of cisco.com is 2001:420:1101:1::a.
B. The Cisco.com website is down.
C. The Cisco.com website is responding with an internal IP.
D. The public IP address of cisco.com is an IPv4 address.
Correct Answer: C
QUESTION 19
What information from HTTP logs can be used to find a threat actor?
A. referer
B. IP address
C. user-agent
D. URL
Correct Answer: C
QUESTION 20
Which of the following are not components of the 5-tuple of a flow in NetFlow? (Select all that apply.)
A. Source IP address
B. Flow record ID
C. Gateway
D. Source port
E. Destination port
Correct Answer: BC
QUESTION 21
You have run a suspicious file in a sandbox analysis tool to see what the file does. The analysis report shows that outbound callouts were made post infection.
Which two pieces of information from the analysis report are needed or required to investigate the callouts? (Choose two.)
A. file size
B. domain names
C. dropped files
D. signatures
E. host IP addresses
Correct Answer: AE
QUESTION 22
What is accomplished in the identification phase of incident handling?
A. determining the responsible user
B. identifying source and destination IP addresses
C. defining the limits of your authority related to a security event
D. determining that a security event has occurred
Correct Answer: D
QUESTION 23
Which regular expression matches “color” and “colour”?
A. col[0-9]+our
B. colo?ur
C. colou?r
D. ]a-z]{7}
Correct Answer: C
QUESTION 24
You see 100 HTTP GET and POST requests for various pages on one of your webservers. The user agent in the requests contain php code that, if executed, creates and writes to a new php file on the webserver. Which category does this event fall under as defined in the Diamond Model of Intrusion?
A. delivery
B. reconnaissance
C. action on objectives
D. installation
E. exploitation
Correct Answer: D
QUESTION 25
During which phase of the forensic process are tools and techniques used to extract the relevant information from the collective data?
A. examination
B. reporting
C. collection
D. investigation
Correct Answer: A
QUESTION 26
Which goal of data normalization is true?
A. Reduce data redundancy.
B. Increase data redundancy.
C. Reduce data availability.
D. Increase data availability
Correct Answer: A
QUESTION 27
What mechanism does the Linux operating system provide to control access to files?
A. privileges required
B. user interaction
C. file permissions
D. access complexity
Correct Answer: C
QUESTION 28
In Microsoft Windows, as files are deleted the space they were allocated eventually is considered available for use by other files. 210-255 dumps This creates alternating used and unused areas of various sizes. What is this called?
A. network file storing
B. free space fragmentation
C. alternate data streaming
D. defragmentation
Correct Answer: B
QUESTION 29
Which of the following is one of the main goals of data normalization?
A. To save duplicate logs for redundancy
B. To purge redundant data while maintaining data integrity
C. To correlate IPS and IDS logs with DNS
D. To correlate IPS/IDS logs with firewall logs
Correct Answer: B
QUESTION 30
A CMS plugin creates two files that are accessible from the Internet myplugin.html and exploitable.php. A newly discovered exploit takes advantage of an injection vulnerability in exploitable.php. To exploit the vulnerability, one must send an HTTP POST with specific variables to exploitable.php. You see traffic to your webserver that consists of only HTTP GET requests to myplugin.html. Which category best describes this activity?
A. weaponization
B. exploitation
C. installation
D. reconnaissance
Correct Answer: B
The best and most updated latest Cisco CCNA Cyber Ops 210-255 dumps exam practice files in PDF format free download from leads4pass. New Cisco CCNA Cyber Ops 210-255 dumps pdf training resources which are the best for clearing 210-255 exam test, and to get certified by Cisco CCNA Cyber Ops. leads4pass 210-255 dumps pdf training materials download free try. It is the best choice for you to pass Cisco 210-255 exam.
Here Are Some Reviews From Our Customers:
You can click here to have a review about us: https://www.resellerratings.com/store/leads4pass
Why Choose Lead4 pass?
leads4pass is the best provider of IT learning materials and the right choice for you to prepare for Cisco CCNA Cyber Ops 210-255 exam. Other brands started earlier, but the price is relatively expensive and the questions are not the newest. leads4pass provide the latest real questions and answers with lowest prices, help you pass Cisco 210-255 exam easily at first try.
